Phishing is a type of deception designed to steal your valuable personal data, such as credit card numbers, passwords, account data, or other information. PayPal, eBay and online banks are common targets. Phishing is typically carried out by e-mail or instant messaging, and often directs users to enter details at a website, although phone contact has also been used.
Phishing E-mail
In brief, a 'phishing' email is one that pretends to be from a company or bank like eBay, PayPal, WAMU, Suntrust etc, and which asks you, (for various reasons), to enter your account data, such as login details. These scams are often supported by fake spoof websites, and victims are tricked into thinking they are logging to a real website. Phishing is a form of identity theft, where fraudsters steal your identity and personal information to gain access to your accounts or commit other crimes using your persona.
Examples:
a.) The following is an example of what a phishing scam e-mail message might look like.
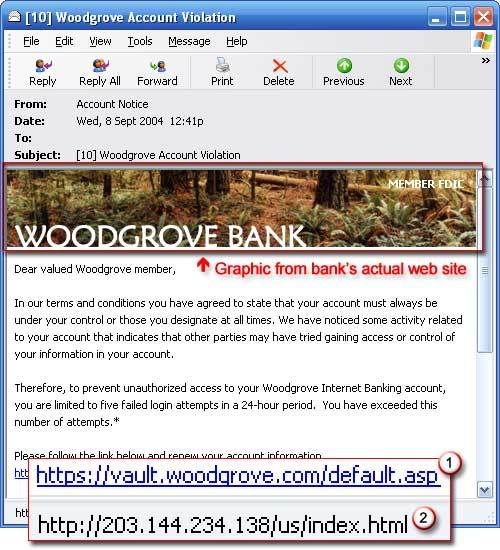
b.) An example of a phishing e-mail, disguised as an official e-mail from a (fictional) bank. The sender is attempting to trick the recipient into revealing secure information by "confirming" it at the phisher's website.
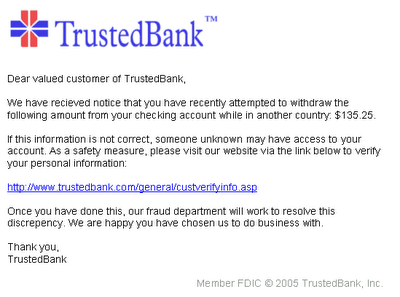
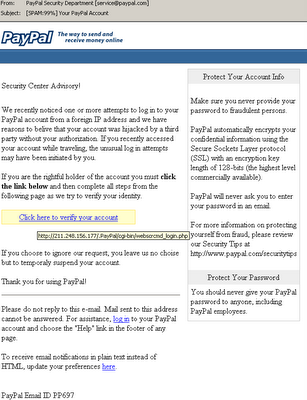
c.) An example of a phishing e-mail targeted at PayPal users.
Phone Phishing
Not all phishing attacks require a fake website. Messages that claimed to be from a bank told users to dial a phone number regarding problems with their bank accounts. Once the phone number (owned by the phisher, and provided by a Voice over IP service) was dialed, prompts told users to enter their account numbers and PIN. Vishing (voice phishing) sometimes uses fake caller-ID data to give the appearance that calls come from a trusted organization.

Prevention Methods:
If you get an email or pop-up message that asks for personal or financial information, do not reply. And don't click on the link in the message, either. Legitimate companies don’t ask for this information via email. If you are concerned about your account, contact the organization mentioned in the email using a telephone number you know to be genuine, or open a new Internet browser session and type in the company’s correct Web address yourself. In any case, don’t cut and paste the link from the message into your Internet browser — phishers can make links look like they go to one place, but
that actually send you to a different site.
Area codes can mislead. Some scammers send an email that appears to be from a legitimate business and ask you to call a phone number to update your account or access a “refund.” Because they use Voice over Internet Protocol technology, the area code you call does not reflect where the scammers really are. If you need to reach an organization you do business with, call the number on your financial statements or on the back of your credit card. In any case, delete random emails that ask you to confirm or divulge your financial information.
Use anti-virus and anti-spyware software, as well as a firewall, and update them all regularly. Some phishing emails contain software that can harm your computer or track your activities on the Internet without your knowledge. Anti-virus software and a firewall can protect you from inadvertently accepting such unwanted files. Anti-virus software scans incoming communications for troublesome files. Look for antivirus software that recognizes current viruses as well as older ones; that can effectively reverse the damage; and that updates automatically. A firewall helps make you invisible on the Internet and blocks all communications from unauthorized sources. It’s especially important to run a firewall if you have a broadband connection. Operating systems (like Windows or Linux) or browsers (like Internet Explorer or Netscape) also may offer free software “patches” to close holes in the system that hackers or phishers could exploit.
Don't email personal or financial information. Email is not a secure method of transmitting personal information. If you initiate a transaction and want to provide your personal or financial information through an organization’s website, look for indicators that the site is secure, like a lock icon on the browser’s status bar or a URL for a website that begins “https:” (the “s” stands for “secure”). Unfortunately, no indicator is foolproof; some phishers have forged security icons.
Review credit card and bank account statements as soon as you receive them to check for unauthorized charges. If your statement is late by more than a couple of days, call your credit card company or bank to confirm your billing address and account balances.
Phishing E-mail
In brief, a 'phishing' email is one that pretends to be from a company or bank like eBay, PayPal, WAMU, Suntrust etc, and which asks you, (for various reasons), to enter your account data, such as login details. These scams are often supported by fake spoof websites, and victims are tricked into thinking they are logging to a real website. Phishing is a form of identity theft, where fraudsters steal your identity and personal information to gain access to your accounts or commit other crimes using your persona.
Examples:
a.) The following is an example of what a phishing scam e-mail message might look like.

b.) An example of a phishing e-mail, disguised as an official e-mail from a (fictional) bank. The sender is attempting to trick the recipient into revealing secure information by "confirming" it at the phisher's website.

c.) An example of a phishing e-mail targeted at PayPal users.

Phone Phishing
Not all phishing attacks require a fake website. Messages that claimed to be from a bank told users to dial a phone number regarding problems with their bank accounts. Once the phone number (owned by the phisher, and provided by a Voice over IP service) was dialed, prompts told users to enter their account numbers and PIN. Vishing (voice phishing) sometimes uses fake caller-ID data to give the appearance that calls come from a trusted organization.

Prevention Methods:
If you get an email or pop-up message that asks for personal or financial information, do not reply. And don't click on the link in the message, either. Legitimate companies don’t ask for this information via email. If you are concerned about your account, contact the organization mentioned in the email using a telephone number you know to be genuine, or open a new Internet browser session and type in the company’s correct Web address yourself. In any case, don’t cut and paste the link from the message into your Internet browser — phishers can make links look like they go to one place, but
that actually send you to a different site.
Area codes can mislead. Some scammers send an email that appears to be from a legitimate business and ask you to call a phone number to update your account or access a “refund.” Because they use Voice over Internet Protocol technology, the area code you call does not reflect where the scammers really are. If you need to reach an organization you do business with, call the number on your financial statements or on the back of your credit card. In any case, delete random emails that ask you to confirm or divulge your financial information.
Use anti-virus and anti-spyware software, as well as a firewall, and update them all regularly. Some phishing emails contain software that can harm your computer or track your activities on the Internet without your knowledge. Anti-virus software and a firewall can protect you from inadvertently accepting such unwanted files. Anti-virus software scans incoming communications for troublesome files. Look for antivirus software that recognizes current viruses as well as older ones; that can effectively reverse the damage; and that updates automatically. A firewall helps make you invisible on the Internet and blocks all communications from unauthorized sources. It’s especially important to run a firewall if you have a broadband connection. Operating systems (like Windows or Linux) or browsers (like Internet Explorer or Netscape) also may offer free software “patches” to close holes in the system that hackers or phishers could exploit.
Don't email personal or financial information. Email is not a secure method of transmitting personal information. If you initiate a transaction and want to provide your personal or financial information through an organization’s website, look for indicators that the site is secure, like a lock icon on the browser’s status bar or a URL for a website that begins “https:” (the “s” stands for “secure”). Unfortunately, no indicator is foolproof; some phishers have forged security icons.
Review credit card and bank account statements as soon as you receive them to check for unauthorized charges. If your statement is late by more than a couple of days, call your credit card company or bank to confirm your billing address and account balances.
Be cautious about opening any attachment or downloading any files from emails you receive, regardless of who sent them. These files can contain viruses or other software that can weaken your computer's security.
Latest Phishing News Headlines:
MillerSmiles cited in Vista book
Yahoo phishing flaw revealed
Anti-Phishing Browsers Not Working
Keylogging Website Trend
Facebook Phishing
Phishing Trend Continues
Tax Phishing Scams
Christmas phishing threats loom
Phishing - A Tougher Art
Google fixes security flaw
Phishing Protection in Office SP2
Yahoo! Hosting Phishing Sites
MillerSmiles cited in Vista book
Yahoo phishing flaw revealed
Anti-Phishing Browsers Not Working
Keylogging Website Trend
Facebook Phishing
Phishing Trend Continues
Tax Phishing Scams
Christmas phishing threats loom
Phishing - A Tougher Art
Google fixes security flaw
Phishing Protection in Office SP2
Yahoo! Hosting Phishing Sites


0 Responses to "Phishing: Examples and its prevention methods"
Post a Comment