Close your eyes, imagine that you switching off your computer at night but waking up to find an error message popped up on your computer screen, followed by innumerable important files become corrupted (especially those files where one documenting their emails containing usernames and passwords). How secure is the data in our computer, merely just by allowing it to access the Internet?
How its work?At first, spammers typed their seedy solicitations into e-mail messages, then displayed them as harder-to-detect graphics. Next came attachments of PDF and Word documents. Now, researchers say, junk-mail purveyors are attaching MP3 files to their missives so users who open them get audio messages about penny stocks, for example. More chatty spam is probably on the way, and it’s likely only a matter of time before video spam invades in-boxes too.
That all for you data, bye bye.
One of the more insidious types of computer virus commandeers a user’s PC, gang pressing it into a network of “bots” that can spew spam, record users’ keystrokes to steal bank account numbers and passwords, or launch attacks against Web sites. Such botnets are getting bigger in size and harder to take down. Case in point: the “Storm Worm” virus that has infected tens of millions of machines this year.
Wait, wait, do you think this is the end? Here more…
Hackers Go Pro??!!In the past few years, hackers have banded together and worked with organized crime to harvest the most valuable data exposed on the Internet. Next year could witness an even more complete merger between the computer and criminal undergrounds. Developers for hire and professional hacking kits are available through online markets. And criminals are on the lookout for intellectual property that resides on companies’ servers. In 2005 and 2006, hackers stole as many as 94 million credit- and debit-card numbers from the computers of retailer TJ Maxx (TJX). More efficient groups could make break-ins like that even more prevalent.
Ok, let conclude the
TOP 10 of online treat...
10. Spam Mail
Spam by e-mail is a type of spam that involves sending identical or nearly identical messages to thousands (or millions) of recipients. Addresses of recipients are often harvested from Usenet postings or web pages, obtained from databases, or simply guessed by using common names and domains.
By definition, spam is sent without the permission of the recipients.
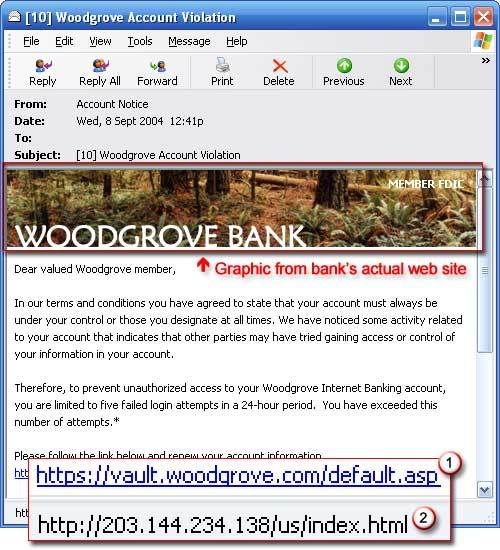
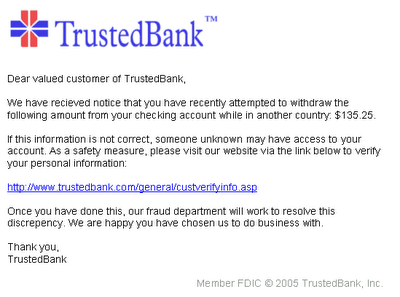
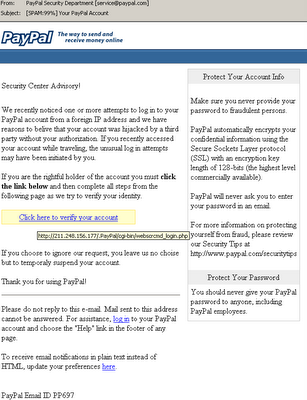
9.Phishing Mail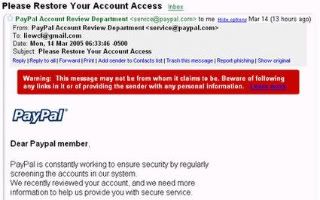
Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and financial account credentials. Phishing messages pretend to be from eBay, PayPal, your bank, or the like. If you log in to their fake sites, they steal your username and password and you’re sunk. However, both IE7 and Firefox 2 have phishing detection built in.
8.Wireless Attact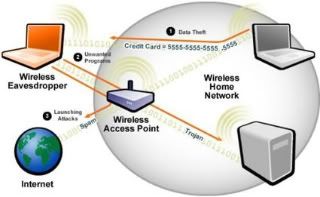
These attacks attempt to penetrate a network by using wireless or evading WLAN access control measures, like AP MAC filters and 802.1X port access controls. If youre not careful, anybody in range can mooch bandwidth from your wireless network and can rum-mage through your files, because they are inside your network. Your routers WPA/WEP encryption can stop the mooching but you have to use it.
7.Hacker Attact
A hacker is a person who accesses computer files without authorisation, often destroying vast amounts of data. Expert hackers dont have times to attack each computers individually. They might broadcast a network virus or release a Trojan, but a personal attack is highly unlikely.
6.Web Exploits
Some Web sites include malicious code to exploit vulnerabilities in your browser or operating system. Just visiting the site can infect or damage your system if the vulnerability hasn’t been patched.
5.Adware
Simple adware pops up ads that get in your face while browsing net can destroy your computer. Most of the adwares records your online activity, phones numbers, contacts and produces ads for you when you go online.
4.Viruses
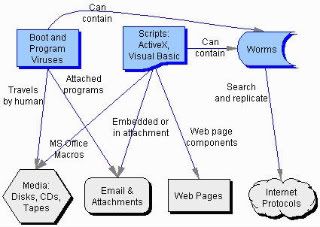
A computer virus is a dangerous computer program with the characteristic feature of being able to generate copies of itself, and thereby spreading. Additionally most computer viruses have a destructive payload that is activated under certain conditions.
3.Spyware/Trojans
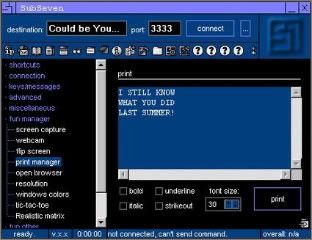
Spyware spies on everything you do and steals private infor-mation. Trojan horse programs pretend to be useful but can turn your computer into a spam-spewing zombie.
2.Identity Theif
Its not just about your computer when they use your credit cards, divert your paycheck, and change your vehicle registration.
1.Social Enginnering
The number one threat to your computers security is you!

Use COMMON SENSE...don't take programs from strangers, don't go to crackz and torrents web sites, and if your security software pops up a warning, READ IT before you click.
If can't, here is another to prevent it, do not use internet.
ME?still need to face this treat, need to post my assignment.
:p


 In the MPH Online.com, the books are divided into 35 categories. People can easily search for the relevant book by clicking on the relevant category. We can choose the book that is most suitable for us because it’s allowed us to view the book description by just click on the book’s icon.
In the MPH Online.com, the books are divided into 35 categories. People can easily search for the relevant book by clicking on the relevant category. We can choose the book that is most suitable for us because it’s allowed us to view the book description by just click on the book’s icon.
 The way to make payment for online purchases is through credit card, Maybank2u.com internet banking and cash or cheque bank in. They accept major credit cards from Visa and MasterCard. These make it easier for the customers to pay for their purchases. For more information on payment, can visit to
The way to make payment for online purchases is through credit card, Maybank2u.com internet banking and cash or cheque bank in. They accept major credit cards from Visa and MasterCard. These make it easier for the customers to pay for their purchases. For more information on payment, can visit to